Advertising disclosure
Hosting Canada is community-supported. We may earn a commission when you make a purchase through one of our links. Read Disclosure.
Uncover Phishing Sites Through Web Analytics
 If you are just getting started with web analytics, you are probably already amazed at what it can do.
If you are just getting started with web analytics, you are probably already amazed at what it can do.
Just by doing some basic analysis on the way that visitors use your website, you can uncover a lot about your target audiences, and how to improve your marketing.
You should also be aware, though, that your web analytics software can be used to achieve far more than this. One of the emerging uses for web analytics software is in detecting and defeating phishing websites.
Recent research has found that the IDs used by web analytics software can be used to detect phishing sites even when these are hidden behind multiple URLs, and this technique is likely to become an important tool for website owners over the next few years.
Criminals are Analysts, Too
![]() The reason why web analytics software is able to detect phishing sites relies on the fact that the criminals who use phishing websites also use web analytics software.
The reason why web analytics software is able to detect phishing sites relies on the fact that the criminals who use phishing websites also use web analytics software.
It might initially sound strange to use this kind of software – more commonly found in marketing departments – to track criminal activity, but it makes total sense.
Phishers are just as interested in the success of their malicious sites as you are in your legitimate one.
In recent research, the research firm Akamai analyzed traffic for 54,261 known phishing sites. A significant proportion of these – 874 domains – had web analytics UIDs associated with them.
A UID is a “Unique Identification” code that web analytics software assigns to customers to track their activity as they move around legitimate sites, and is what makes this kind of software so useful for website owners.
The fact that these UIDs also appear on phishing sites is due to two reasons. Some criminals are clearly using web analytics software to track the performance of their fake sites. In some other cases, these IDs may have been copied from legitimate sites as scammers have duplicated them.
Using UIDs to Detect Phishing
Phishing attacks have developed significantly over the past few years, to the extent that they now make use of advanced social engineering techniques. This social angle works like magic to trick a user into entering sensitive information into a fake website.
Typical cybersecurity recommendations, such as a firewall and antivirus suite to form a defensive perimeter, combined with the encryption-based features of a quality VPN, can’t do a thing to protect against a human operator who clicks on a link that they shouldn’t have.
The problem is that phishing sites don’t just use one fake URL anymore. Instead, phishing attacks are generally large-scale operations that make use of many pages distributed across multiple servers and domains.
If a security team discovers that a URL is associated with a phishing site, it is simple enough to block access to this single URL, but what if the same site exists in many different copies across a huge range of locations?
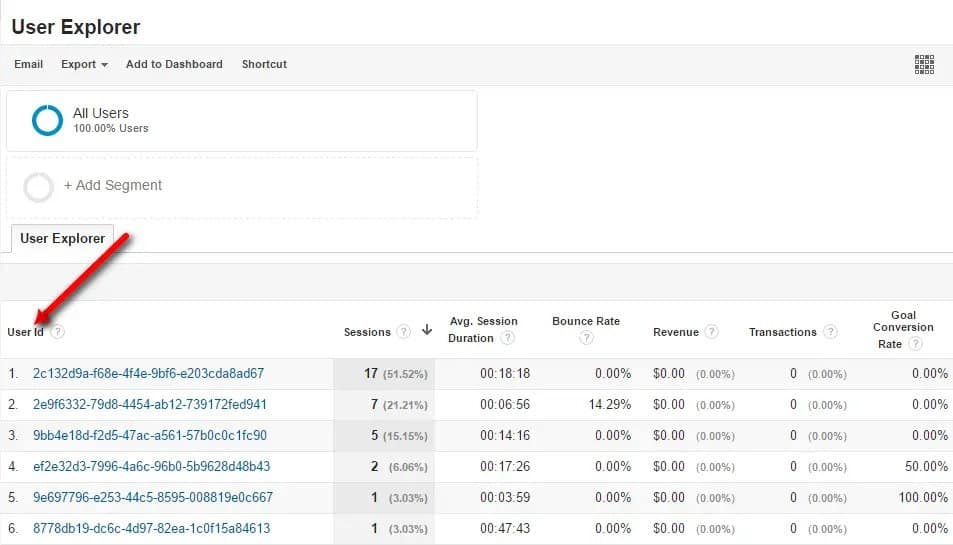
That’s where web analytics UIDs come in. If the scammer is using the same UIDs across multiple fake sites, it is possible to detect this. The sites can then be associated with the scammer, and all of them can be blocked. This is similar to how phishing filters work but takes an analysis of the phishing sites to the next level.
In addition, the UIDs that phishers sometimes accidentally leave in their code can help the legitimate owners of cloned sites to track down phishing scams. Lazy scammers just copy across the same UIDs that are in use by the affected site, and these can be used to prove that it has been copied.
In some cases, legitimate websites even see a phishing site’s activity in its own web analytics portal, which makes reporting these scam sites to a domain registrar even easier.
Real-Life Examples
The recent research also provides some real-life examples of where web analytics helped researchers at Akamai to discover large-scale phishing campaigns, including a scam that targeted LinkedIn users.
Users on this networking site were targeted with dozens of “fake”, misleading URLs. There was very little evidence that these URLs were being used by the same attacker, except for the fact that every single one had the same Google analytics UID associated with it.
This made it easy for Akamai to assess the extent of the attack, and build filters that would block these sites.
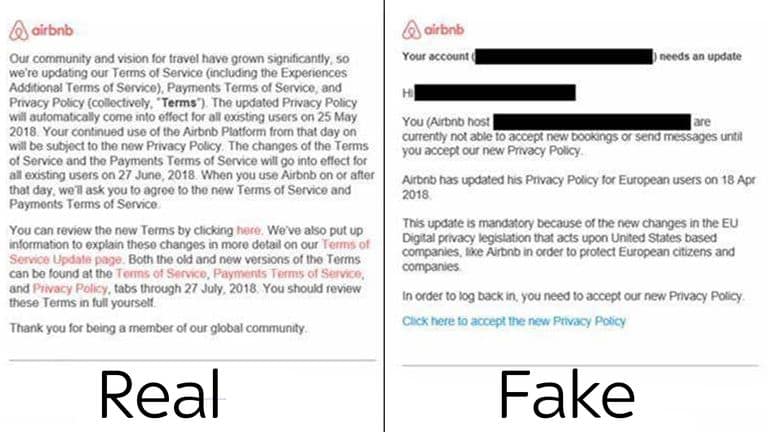
A second example was a phishing campaign that was designed to rip off AirBnB users. This scam aimed to redirect users to subdomains on 000webhostapp.com, which is itself a legitimate web hosting service.
The “problem”, from the scammers’ point of view, was that they had accidentally copied over the code that generates UIDs from the site they had copied – AirBnB – and so AirBnB staff saw the malicious sites in their web analytics portal.
“Enterprise security teams can track their own analytic UIDs that are being used in the wild as the result of their website content being copied for building phishing website,” Akamai Security Researcher Tomer Shlomo tells CSO via email.
“Security researchers and security vendors will use phishing Toolkit UIDs which will give them the ability to track other phishing websites and the ability to assess the scale of the campaign or find other phishing activities deployed by the same threat actor.”
Web Analytics and Cyberdefense
Though the idea of using web analytics software for defending yourself against cyberattacks is a relatively new one, it should come as no surprise that analysis software can help you keep your website secure.
Ultimately, cybersecurity is about collecting as much information as possible on the way that your site operates, and web analytics is a powerful tool for this kind of collection and analysis.
So while some web analytics challenges remain, you should also recognize that web analytics is not merely a reactive auditing tool: it can also be used proactively to identify phishing sites and protect yourself against them.